Locations:
Breakfasts/reception/dinners : Macdonald D
All sessions : Macdonald E/F
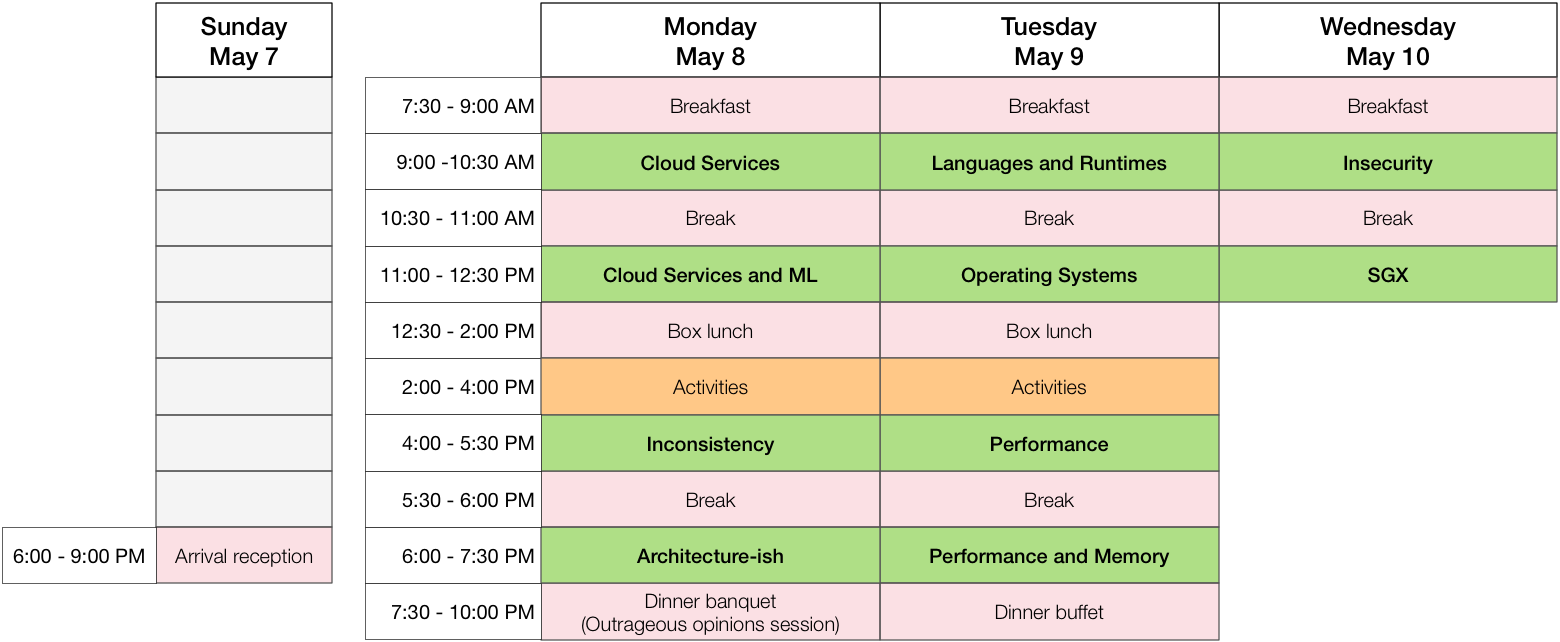
Sunday (May 7)
18:00 - 21:00 : Arrival reception (snacks and bar)
Monday (May 8)
07:30 - 09:00 : Breakfast
09:00 - 10:30 : Cloud Services (chair: Andy Warfield)
| Thinking about Availability in Large Service Infrastructures |
| Jeffrey C. Mogul, Rebecca Isaacs, Brent Welch (Google) |
| Gray Failure: The Achilles' Heel of Cloud-Scale Systems |
| Peng Huang (Microsoft Research, JHU), Chuanxiong Guo, Lidong Zhou, Jacob R. Lorch (Microsoft Research), Yingnong Dang, Murali Chintalapati, Randolph Yao (Microsoft Azure) |
| Verification in the Age of Microservices |
| Aurojit Panda (UC Berkeley); Mooly Sagiv (Tel Aviv University); Scott Shenker (UC Berkeley/ICSI) |
10:30 - 11:00 : Coffee break
11:00 - 12:30 : Cloud Services and ML (chair: Derek Murray)
| Will Serverless End the Dominance of Linux in the Cloud? |
| Ricardo Koller, Dan Williams (IBM T.J. Watson Research Center) |
| No!: Not Another Deep Learning Framework |
| Linh Nguyen, Peifeng Yu, Mosharaf Chowdhury (University of Michigan) |
| Real-Time Machine Learning: The Missing Pieces |
| Robert Nishihara, Philipp Moritz, Stephanie Wang, Alexey Tumanov, William Paul, Johann Schleier-Smith, Richard Liaw, Michael I. Jordan, Ion Stoica (UC Berkeley) |
12:30 - 14:00 : Box lunch
14:00 - 16:00 : Mid-day activities
16:00 - 17:30 : Inconsistency (chair: Kim Keeton)
| Consistency Oracles: Towards an Interactive and Flexible Consistency Model Specification |
| Beom Heyn Kim, Sukwon Oh, David Lie (University of Toronto) |
| From Crash Consistency to Transactions |
| Yige Hu, Youngjin Kwon, Vijay Chidambaram, Emmett Witchel (University of Texas at Austin) |
| Flash Drive Lifespan *is* a Problem |
| Tao Zhang (University of North Carolina at Chapel Hill); Aviad Zuck (Technion - Israel Institute of Technology); Donald E. Porter (University of North Carolina at Chapel Hill); Dan Tsafrir (Technion - Israel Institute of Technology) |
17:30 - 18:00 : Coffee break
18:00 - 19:30 : Architecture-ish (chair: Michael Stumm)
| OmniX: an accelerator-centric OS for omni-programmable systems |
| Mark Silberstein (Technion - Israel Institute of Technology) |
| Quantum Operating Systems |
| Henry Corrigan-Gibbs, David J. Wu, Dan Boneh (Stanford University) |
| It's Time to Think About an Operating System for Near Data Processing Architectures |
| Antonio Barbalace, Anthony Iliopoulos, Holm Rauchfuss, Goetz Brasche (Huawei Research) |
19:30 - 22:00 : Dinner banquet (and outrageous opinions session)
Tuesday (May 9)
07:30 - 09:00 : Breakfast (Macdonald D)
09:00 - 10:30 : Languages and Runtimes (chair: Ivan Beschastnikh)
| Return of the Runtimes: Rethinking the Language Runtime System for the Cloud 3.0 Era |
| Martin Maas, Krste Asanovic, John Kubiatowicz (University of California, Berkeley) |
| System Programming in Rust: Beyond Safety |
| Abhiram Balasubramanian, Marek S. Baranowski (University of Utah); Anton Burtsev (UC Irvine); Aurojit Panda (UC Berkeley); Zvonimir Rakamarić (University of Utah); Leonid Ryzhyk (VMware Research) |
| Towards Automated Configuration of Systems with Non-Functional Constraints |
| Linda Leuschner, Martin Küttler, Tobias Stumpf, Christel Baier, Hermann Härtig, Sascha Klüppelholz (TU Dresden) |
10:30 - 11:00 : Coffee break
11:00 - 12:30 : Operating Systems (chair: Chris Rossbach)
| Towards Proving Optimistic Multicore Schedulers |
| Baptiste Lepers (EPFL); Gilles Muller, Julia Lawall (LIP6); Willy Zwaenepoel (EPFL); Jean Pierre Lozi (Université Nice Sophia-Antipolis); Nicolas Palix (Université Grenoble Alpes); Redha Gouicem, Julien Sopena (LIP6) |
| Hypercallbacks: Decoupling Policy Decisions and Execution |
| Nadav Amit (VMware Research); Michael Wei (VMware Research, UC San Diego); William Tu (VMware) |
| OS Support for Thread Migration and Distribution in the Fully Heterogeneous Datacenter |
| Pierre Olivier, Sang-Hoon Kim, Binoy Ravindran (Virginia Tech) |
12:30 - 14:00 : Box lunch
14:00 - 16:00 : Mid-day activities
16:00 - 17:30 : Performance (chair: Sasha Fedorova)
| A Case Against Tiny Tasks in Iterative Analytics |
| Ehsan Totoni, Subramanya R Dulloor, Amitabha Roy (Intel Labs) |
| Performance clarity as a first-class design principle |
| Kay Ousterhout (UC Berkeley); Christopher Canel (Carnegie Mellon University); Max Wolffe, Sylvia Ratnasamy (UC Berkeley); Scott Shenker (UC Berkeley, ICSI) |
| Scalability Bugs: When 100-Node Testing is Not Enough |
| Tanakorn Leesatapornwongsa, Cesar A. Stuardo, Riza O. Suminto, Huan Ke, Jeffrey F. Lukman, Haryadi S. Gunawi (University of Chicago) |
17:30 - 18:00 : Coffee break
18:00 - 19:30 : Performance and Memory (chair: Don Porter)
| The Game of Twenty Questions: Do You Know Where to Log? |
| Xu Zhao, Kirk Rodrigues, Yu Luo, Michael Stumm, Ding Yuan (University of Toronto); Yuanyuan Zhou (University of California, San Diego) |
| Separating Translation from Protection in Address Spaces with Dynamic Remapping |
| Reto Achermann (ETH Zurich); Chris Dalton, Paolo Faraboschi (Hewlett Packard Labs); Moritz Hoffmann (ETH Zurich); Dejan Milojicic, Geoffrey Ndu (Hewlett Packard Labs); Alexander Richardson (University of Cambridge); Timothy Roscoe (ETH Zurich); Adrian L. Shaw (Hewlett Packard Labs); Robert N. M. Watson (University of Cambridge) |
| Towards O(1) Memory |
| Michael M Swift (University of Wisconsin--Madison) |
19:30 - 22:00 : Dinner buffet
Wednesday (May 10)
07:30 - 09:00 : Breakfast (Macdonald D)
09:00 - 10:30 : Insecurity (chair: Peter Druschel)
| Preserving Hidden Data with an Ever-Changing Disk |
| Aviad Zuck, Udi Shriki (Technion - Israel Institute of Technology); Donald E. Porter (University of North Carolina at Chapel Hill); Dan Tsafrir (Technion - Israel Institute of Technology) |
| A Clairvoyant Approach to Evaluating Software (In)Security |
| Bhushan Jain (University of North Carolina at Chapel Hill); Chia-che Tsai (Stony Brook University); Donald E. Porter (University of North Carolina at Chapel Hill) |
| Why Your Encrypted Database Is Not Secure |
| Paul Grubbs, Thomas Ristenpart, Vitaly Shmatikov (Cornell Tech) |
10:30 - 11:00 : Coffee break
11:00 - 12:30 : SGX (chair: Michael Kaminsky)
| Glimmers: Resolving the Privacy/Trust Quagmire |
| David Lie (University of Toronto/Google); Petros Maniatis (Google) |
| Hardware is the new Software |
| Andrew Baumann (Microsoft Research) |